Detect & Response

Detect & Respond:
In today’s hyper connected age, cyber security breaches are becoming more commonplace. The growing interconnectivity between users, devices, and networks is giving rise to new security vulnerabilities with each passing day. Cybercriminals have become smarter and more sophisticated, using advanced technologies such as AI and innovative attack methodologies such as social engineering to create and launch more powerful attacks. Thus, Cyber Threat Intelligence Dubai is the knowledge that allows you to prevent or mitigate cyber-attacks by analyzing threat data and providing information on adversaries. Providing information about attackers, their motives, and their capabilities helps identify, prepare, and prevent attacks.
How does cyber threat intelligence work?
When it comes to cyber-attacks, organizations can be proactive rather than reactive by utilizing threat intelligence. Cyber-attacks cannot be effectively combated without understanding security vulnerabilities, threat indicators, and threats. Cyber intelligence: security professionals can prevent and contain attacks faster when they use cyber intelligence, potentially saving the cost of a cyberattack if it occurs.
Types of threat intelligence:
It is important to note that there are three types of threat intelligence - strategic, tactical, and operational.
Strategic threat intelligence:
It's typically aimed at non-technical audiences, likewise the organization's circle. Often, strategic threat intelligence is derived from open sources - which means that anyone can access them - such as media reports, white papers, and research and development projects.
Tactical threat intelligence:
Designed for a more technically proficient audience, this focuses on the immediate future. Intelligence gathered through tactical operations is the most straightforward form of intelligence to generate and is usually automated. Because many IOCs become obsolete very quickly, they can often have a short lifespan.
Operational threat intelligence:
As part of operational threat intelligence, we study past cyber-attacks and conclude the intent, timing, and sophistication of these cyber-attacks to answer these questions. Getting operational threat intelligence requires more resources than tactics, techniques, and procedures because they can change their tools so quickly.
Cyber Attack Incident Response: How important is it?
A structured incident response approach is used to address various types of security incidents, cyber threats, and data breaches. Using Cyber Incident Response Dubai methodologies, cyberattacks and live incidents can be identified, contained, and minimized. It is important to note that a well-built incident response plan can provide a solution to a potential vulnerability that can prevent future attacks. In Incident Handling, Response refers to logistics, communications, synchronicity, and planning required to resolve an incident.
It is, in short, a scary time to be an enterprise.
This is where Ahad’s Cyber Security Framework steps into the picture. Our Cyber Response and Investigation teams work closely with clients to proactively identify potential threats and vulnerabilities, as well as to detect respond to ongoing breaches. We help you contain security breaches and mitigate their impact on your business and data. We also conduct detailed forensic investigations into security events to design and implement a robust threat detection and response strategy to combat future attacks. Our digital forensics teams also provide exhaustive and reliable forensic and expert witness services, covering everything from investigation strategy and planning, scoping and collection to analysis and presentation of material to court.

Real-world Challenges: How ready are you to face cyber threats?
If you are wondering whether you need to improve your enterprise’s threat detection and response capabilities, consider the following questions:
- Has my organization’s cybersecurity already been compromised by malicious insiders that are abusing their position and system access for any illegal activity?
- How to determine whether I am a potential target of data breaches and attacks from criminal gangs, competitors, or nation-states?
- Is my business capable of recovering from worms, malware, or other attacks that take over workstations and systems?
- What steps do I take if I don’t have the required capability to respond to a cyber-attack?
- In case of an attack, how do I determine and prove the course of its events?
- How can the integrity and provenance of electronic data which is being used in investigative or litigation proceedings, be proven?
If you are unsure about your response to any of these questions, you might want to re-evaluate your approach to enterprise security.
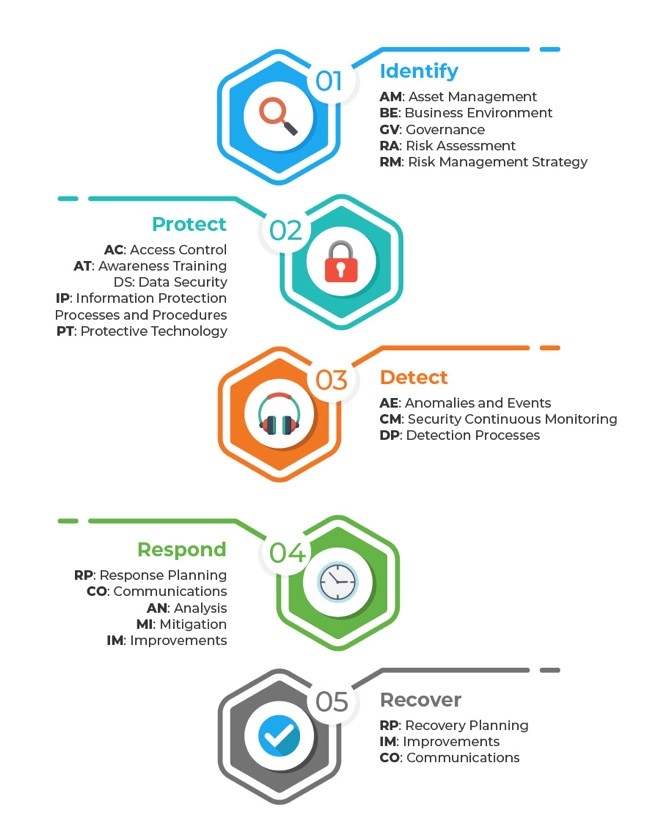
Here is how Ahad’s Cyber Security Framework works
- Identify
You can’t solve a problem you don’t know about, which is why identifying potential threats and attacks should be a priority. This can only be achieved with a proactive approach to managing potential risks and threat exposure. You need a comprehensive, real-time view of your network, devices, users, and data – and how they are connected with and influence each other. Such constant analysis and evaluation of your security health are integral to implementing well-defined security policies and processes which help in managing and mitigating risk.
- Detect
Timing is a crucial factor in the event of a security breach. Real-time threat assessment and vulnerability evaluation can improve network visibility and transparency to enable near-instant threat detection. This can help you respond faster to security incidents on a near-instant basis, enabling you to contain breaches and attacks at their point of incidence while minimizing the overall impact on your operations.
- Protect
In 2019, enterprises paid, on average, $3.92 million to address security breaches. This means but one thing: security breaches are costly affairs that hurt your revenues and your market reputation. Implementing strong cybersecurity measures, processes, and policies can help you protect yourself from the impact of a successful breach on your business and reputation. These include tracking access to digital and physical resources, providing security awareness and sensitivity training, focusing on data security, and managing and monitoring network configurations, and deploying cutting-edge cybersecurity solutions.
- Respond
Despite the precautions taken, your business may still be breached. Protecting your organization, in this scenario, requires a well-thought-out, strong response plan that outlines specific guidelines and strategies in case of a breach. Post-event response also needs to be mapped out well in advance – from measures and solutions implemented to prevent a future breach to a media action plan regarding the handling of public perception about the security event.
- Recover
Recovering your operations is a priority after every breach. A robust recovery plan can help you restore operational capacity and enterprise-critical data, as well as to communicate essential information to your employees and other stakeholders. It also analyzes key learnings from the latest event to update playbooks and response strategies, thus ensuring that your business can bounce back up from a breach much stronger and resilient than ever before.