IoT Security in the Era of 5G A Growing Challenge
IoT Security in the Era of 5G A Growing Challenge

The introduction of 5G technology has marked a new chapter in connectivity, allowing a wide range of Internet of Things (IoT) devices to interact effortlessly. Although this enhanced connectivity brings many advantages, it also presents fresh security challenges. The distinct features of 5G networks, combined with the varied nature of IoT devices, result in a complex environment that demands careful security considerations.
Key Security Concerns in 5G IoT:
-
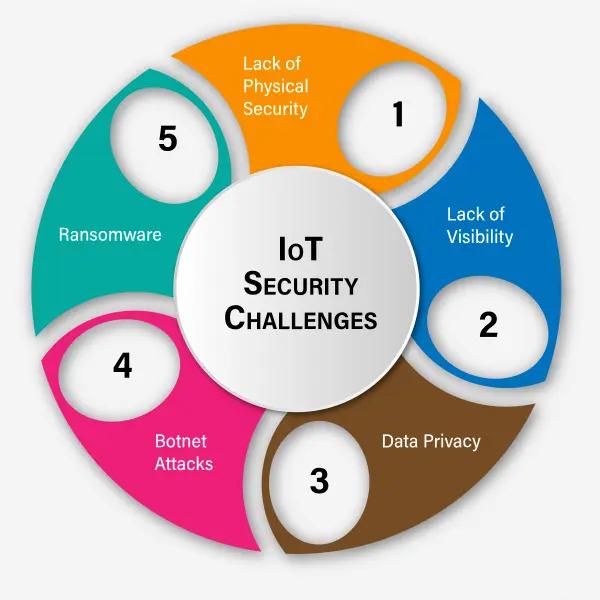
Expanded Attack Surface: The sheer volume of interconnected IoT devices greatly enlarges the potential attack surface, providing more opportunities for malicious actors to exploit vulnerable systems.
-
Data Privacy and Protection: IoT devices frequently gather and transmit sensitive information, making it crucial to safeguard against data breaches and unauthorized access.
-
Network Vulnerabilities: The complexity of 5G networks brings new vulnerabilities that attackers could potentially exploit.
-
Software and Firmware Weaknesses: Many IoT devices operate on outdated or inadequately secured software and firmware, leaving them open to attacks.
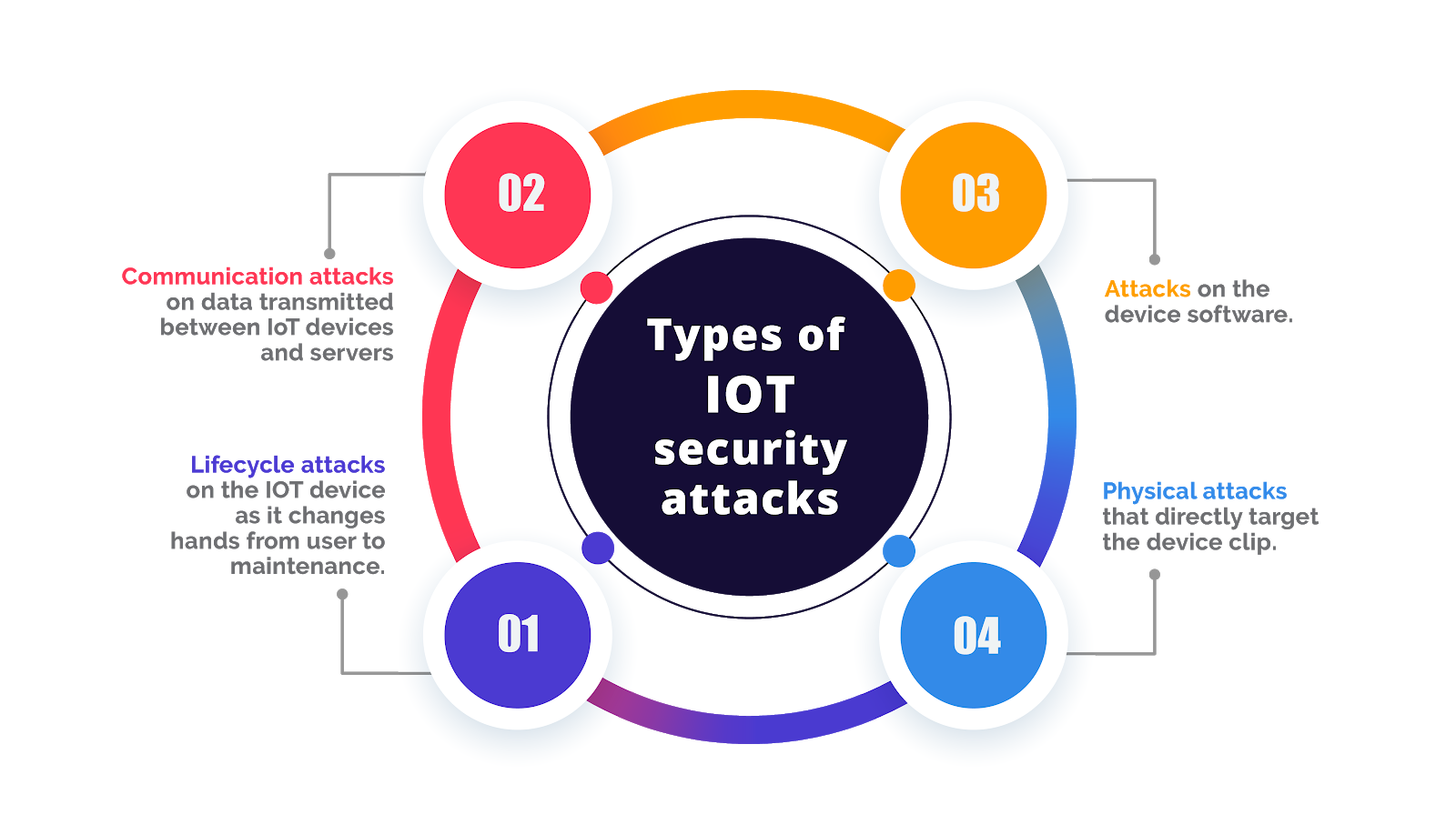
Addressing IoT Security Challenges in the 5G Era
To mitigate the risks associated with 5G and IoT, a comprehensive security strategy is essential:
-
Enhanced Device Security: Manufacturers must prioritize creating IoT devices with secure hardware and software, incorporating features like encryption, authentication, and intrusion detection.
-
Secure Network Infrastructure: 5G network operators should implement stringent security measures to prevent unauthorized access and data breaches.
-
Consistent Updates and Patches: Regularly update IoT devices and their software with the latest security patches to fix known vulnerabilities.
-
Protected Data Transmission: Ensure that data sent over 5G networks is encrypted to guard against eavesdropping and data interception.
-
User Education and Awareness: Educate users on IoT security best practices, such as using strong passwords, avoiding public Wi-Fi, and being aware of phishing threats.
-
Collaboration and Standardization: Promote collaboration among industry stakeholders to establish common security standards and best practices for 5G IoT.
The Road Ahead
As 5G technology advances, staying alert to emerging security threats is crucial. By taking a proactive stance and implementing strong security measures, we can fully harness the benefits of 5G IoT while minimizing potential risks.
AHAD specializes in IoT security solutions and services. Let us help you safeguard your business. Contact us for a consultation!
