Evidence of SolarWinds Vulnerabilities on the Darknet
Evidence of SolarWinds Vulnerabilities on the Darknet

In light of the large-scale nation-state sponsored attack against U.S. government networks, and critical commercial sectors of the U.S. supply chain, our analysts reviewed historical darknet content for any SolarWinds related activity. We uncovered an extensive amount of content containing SolarWinds and Orion-specific vulnerabilities and zero-days across darknet exploit marketplaces and discussion forums, many of which could be devastating if exploited at scale.
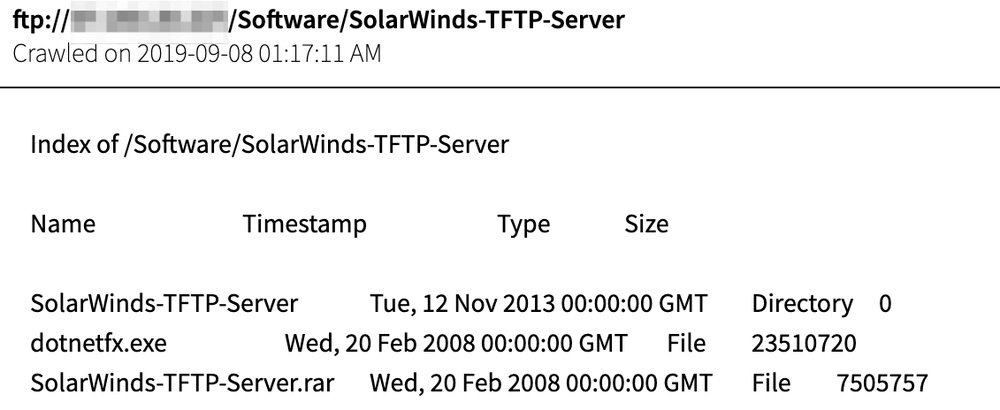
Most notably, DarkOwl analysts also uncovered SolarWinds product documentation and application executables stored on unsecured FTP servers successfully collected by DarkOwl’s platform back in late 2019. The FTP servers contained not only SolarWinds-specific server files, but also Microsoft’s dotnetfx.exe file, a critical executable for installing operating system updates.

Upon further investigation, we traced the IP address of these open FTP servers to the internet service provider, JSC "Severen-Telecom" (severen.ru) in the Northwestern Federal District of Saint Petersburg, Russia.
In addition to the potential tie linking these files to campaigns conducted out Russia, we also have a great deal of evidence to show a suspicious amount of interest in SolarWinds vulnerabilities across the deep web and darknet. In fact, based on the extent of our analysts findings on the darknet alone, we have reason to believe that SolarWinds has likely been a cyber target for quite some time, though a large extent of these indicators that SolarWinds was being targeted transpired in late 2019 and early 2020. For example DarkOwl Vision has collected 98 documents from a single popular zero-day marketplace with mentions of SolarWinds-specific vulnerabilities since February 2020 (shown below).

Example of SolarWinds Cross Site Scripting Vulnerability, posted on the darknet in May of 2020
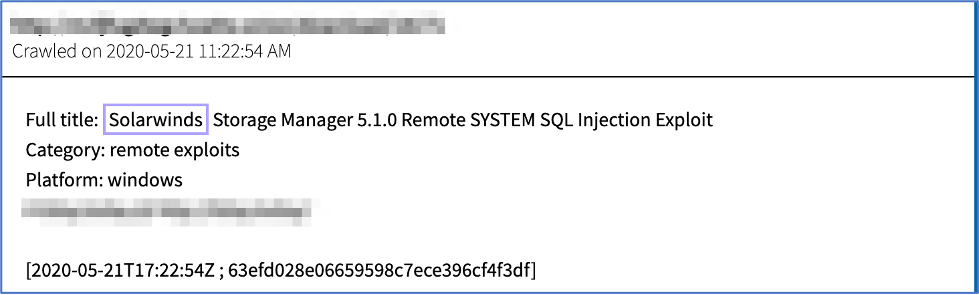
Example of SolarWinds SQL Injection Exploit, posted on the darknet in May of 2020
In addition, our analysts have also noted that there was a great number of users on deep web forums that have displayed a particular interest in understanding critical information security applications and intrusion detection systems, with shares of ‘cracked’ versions of SolarWinds Security Event Manager application as recently as July 2020 (pictured below).

In recent days, DarkOwl has witnessed several darknet users across English and Russian-speaking forums discussing key open source reporting regarding the attack, more specifically, Vinoth Kumar’s posted to social media that he uncovered a public Github repo leaking credentials belonging to SolarWinds since June 2018.

